Qualcomm Chips' Vulnerabilities Let Hackers Steal Sensitive Data From Samsung, LG, and Motorola Phones
Aadhya Khatri - Nov 19, 2019

Qualcomm CPUs, on which most Android smartphones run, has a vulnerability that may allow bad actors stealing users' most sensitive data
- Qualcomm Announces Snapdragon 870; To Debut Soon In Xiaomi, OnePlus, Motorola Smartphones
- Qualcomm Announced Snapdragon 888, The Next Mobile Chip For High-End Smartphones
- At Least Five Smartphones Will Feature Snapdragon 875 & 100W+ Charging Support, New Leak Says
Experts have found a flaw in chips manufactured by Qualcomm that may allow attackers to steal vital information.
The report revealed that Qualcomm CPUs, on which most Android smartphones run, has a vulnerability that may result in the execution of Advanced Persistent Threats, bootloader unlocking, and device rooting.
The finding was announced at Recon Montreal, a conference on computer security that focuses on advanced techniques on exploitation and reverse engineering.
After this revelation, Qualcomm has fixed all the known vulnerabilities. LG and Samsung have also issued the patches, and Motorola is reportedly working to find a fix.
According to Qualcomm, all of the flaws have been fixed, one of them back in November 2014, and another in October this year. While the company receives no report of ongoing exploitation, it still encourages users to download updates with patches provided by OEMs. It also emphasizes that one of Qualcomm’s priorities is to offer technologies to support privacy and security.

A few months ago, Qualcomm also patched a flaw that let hackers stealing encryption keys and private data in the secure world of the chipset.
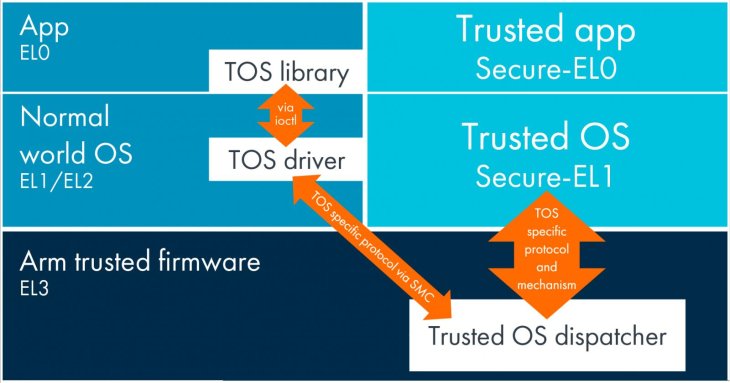
Qualcomm’s chips always come equipped with a TEE (stand for Trusted Execution Environment), a secure area, which makes certain data and code’s integrity and confidentiality.
Qualcomm Trusted Execution Environment is built on ARM TrustZone technology, which works to protect vital data from being compromised.
The secure world also offers extra services like truslets, another word for trusted third-party components. These trustlets serves as a bridge connecting the real world where Android occupies and the Trusted Execution Environment, enabling data transferring between these worlds.
The Trusted World is where sensitive data is stored, we are talking about storage encryption keys and credit card information. It is also the last defense standing in between your data and bad actors. If it is compromised, there is stopping hackers from laying their hands on your most precious data.
Qualcomm said that if the hackers did not have the hardware keys of the device, they could not steal what QTEE stored in its trusted world. The only possibility is that these data are exposed on purpose.

However, the contrary is proven by research lasting for four months. So, in reality, the TEE can be penetrated, unlike what Qualcomm announced.
To proves so, the researchers behind the finding made use of fuzzing, a method involving autonomously feeding the machine with random data to overload it and then crash it. After that, any potential flaws and errors that might allow breaches will be exposed.
The fuzzing method, in this case, aimed at Samsung’s, LG’s, and Motorola’s implementation of trustlets, or in other words, the code in charge of confirming the trustlets’ integrity, revealing several vulnerabilities along the way.
These flaws can let hackers load the secure world with patched trusted apps, run trusted apps outside of the TEE, and many more.
These attacks targeting TEEs have shown what hackers can do to steal users’ data. However, for now, we have not had any evidence of these flaws being used in real life. However, it does not mean we should let our guard down as TEEs are so promising a target that hackers cannot afford to ignore.
Any attempt to attack the TrustZone may allow bad actors to gain access to the most sensitive data stored on a smartphone or tablet, which can have a devastating effect on users’ life.
Featured Stories

ICT News - Mar 05, 2026
X Platform Implements Strict Measures Against Fake AI-Generated Videos Amid Iran...

How To - Mar 04, 2026
Getting Started with AI: A Newbie's Simple Guide

ICT News - Mar 03, 2026
Budget Entry-Level PCs Under $500 to Vanish by 2028 Due to Memory Price Surge

ICT News - Mar 02, 2026
IDC Report Predicts Surging Smartphone Prices Due to Global RAM Shortage

ICT News - Mar 01, 2026
Samsung Links Galaxy S26 Price Hikes to AI Memory Supply Issues

ICT News - Feb 28, 2026
Anthropic Blacklisted by US Department of War: Trump Orders Federal Ban Over AI...

ICT News - Feb 26, 2026
AI Models Frequently Resort to Nuclear Escalation in Simulated Crises, Study...

ICT News - Feb 23, 2026
It's Over for Xbox: Asha Sharma Takes Over to Ruin Microsoft Gaming with AI

ICT News - Feb 22, 2026
Which AI Model Excels at Which Task in 2026: A Comprehensive Guide

ICT News - Feb 21, 2026
AI Coding Agent Causes Major AWS Outage at Amazon
Read more

Gadgets- Mar 08, 2026
Best Budget Keyboards of 2026
These budget keyboards prove that you don't need to spend hundreds for a quality typing experience in 2026.

Mobile- Mar 08, 2026
Transforming Android: New Desktop Mode Makes Phones PC-Capable
This update marks an exciting era for Android, empowering users to do more with their everyday devices.
Comments
Sort by Newest | Popular