Indian Man Rewared Rs 75.3 Lakh For Finding A Dangerous Bug In Sign In With Apple
Dhir Acharya - Jun 01, 2020

Apple has paid a Rs 75.3 lakh ($100,000) bounty to developer Bhavuk Jain for finding a major bug in Apple's login system, “Sign in with Apple.”
- Best Gaming Phones 2025: Top Devices for Mobile Gaming
- Apple Kills Original HomePod, Focusing On HomePod Mini
- iPhone 12 Color Is Fading Away Quickly And No One Knows Why
Apple has paid a Rs 75.3 lakh ($100,000) bounty to developer Bhavuk Jain for finding a major bug in Apple's login system, “Sign in with Apple.” The discovered bug could have let bad actors take over an account on certain apps and websites.
Jain said that the bug was related to how the iPhone maker was validating users when using Sign in with Apple. Released in 2019, the system can be used with Apple IDs, meant to help users avoid being tracked through using other login services, Google and Facebook for example. One key selling point of this login system is the ability to hide users’ emails from third parties.
Sign in with Apple authorizes a user by using a JSON Web Token (JWT), a code created by Apple’s servers. During the authorization process in an app, Apple allows users to opt for sharing or hiding their Apple ID with that third party. If the user chooses not to share with an app, the system will generate an Apple email ID for the user to use in that service.
Once the authorization is completed, depending on the user’s choice, Apple will generate a JWT containing the email ID. They can log into the third-party app using this email ID. And here’s where the bug attacks.
According to Jain, he found in April that he could request a JWT for any Apple email ID.
“When the signature of these tokens was verified using Apple’s public key, they showed as valid. This means an attacker could forge a JWT by linking any email ID to it and gaining access to the victim’s account.”
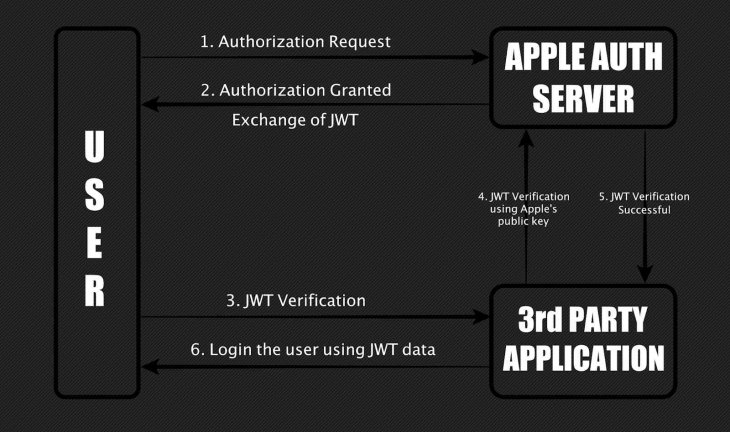
The Hacker News reported that the developer found the cause of this: users were required to log into their Apple accounts before the authorization request was initiated. The system wasn’t validating if the same person requested a token in the next step from its authentication server.
This bug affected third-party apps that were using the system instead of implementing their own additional security measures.
As pointed out by the Hacker News, this vulnerability could be exploited by bad actors even if the user opted for hiding their Apple email ID from third parties and that they could use the flaw to sign up a new account with their victim’s Apple ID.
Jain explained that this vulnerability is serious because it could have let a bad actor completely take over an account. Many developers have integrated Sign in with Apple as it’s mandatory for apps supporting other social logins like Giphy, Spotify, Dropbox, and Airbnb.
According to Jain, Apple had conducted an investigation and said it didn’t find any account compromise or misuse due to this vulnerability.
Featured Stories

ICT News - Jul 05, 2025
Windows 11 is Now the Most Popular Desktop OS in the World

ICT News - Jul 02, 2025
All About Florida’s Alligator Alcatraz: A Smart Move for Immigration Control

ICT News - Jun 25, 2025
AI Intimidation Tactics: CEOs Turn Flawed Technology Into Employee Fear Machine

ICT News - Jun 24, 2025
Tesla Robotaxi Finally Hits the Streets: $4.20 Rides That'll Make You Hold Your...

ICT News - Jun 24, 2025
World's First Flying Humanoid Robot Takes Flight

ICT News - Jun 24, 2025
When Closed Source Met Open Source: Bill Gates Finally Meets Linus Torvalds After...

Gadgets - Jun 23, 2025
COLORFUL SMART 900 AI Mini PC: Compact Power for Content Creation

ICT News - Jun 22, 2025
Neuralink Telepathy Chip Enables Quadriplegic Rob Greiner to Control Games with...

ICT News - Jun 20, 2025
Tesla vs Zoox vs Waymo: Who would win?

ICT News - Jun 19, 2025
Comments
Sort by Newest | Popular