WhatsApp's Rival Telegram Is Prone To Hacking Through Voicemail Backdoor
Chitanis - Aug 05, 2019

Last week, 4 suspects were arrested for hacking into more than 1,000 Telegram accounts – WhatsApp’s rival.
- 3.2 Billion Email And Password Pairs Have Been Leaked, Here's How To Check If You Are Affected
- Watch This Man Hack 26 iPhones At The Same Time Without Even Touching Them
- China Attacked Indian Satellite Systems Several Times In The Last Decade
Telegram has rightly been famous for protecting its users’ privacy with high privacy. However, according to recent reports, the company definitely cannot prevent targeted hacking. Last week, four suspects were arrested for hacking into more than 1,000 accounts of Telegram. The account holders which were hacked into include not only Ministers Paulo Guedes and Sergio Moro, but also Jair Bolsonaro, Brazil’s President. Four suspects were alleged to use an uncommon trick to hack into their target accounts from their mobile phones.

As reported by Naked Security, Telegram is prone to account takeover by hackers, especially when these hackers are pretending to be the user to receive a new phone SIM along with the phone number of their targets. Finally, after downloading Telegram and using the verification system through SMS, the account is taken over.
Nevertheless, according to Naked Security, hacking through voicemail is another method, which is why many people couldn’t protect their own accounts because they actually didn’t know that their voicemail was exploited and also, voicemail isn’t provided as a service in Telegram.

Walter Delgatti Neto – 30 years old – is a suspect who was arrested. Reportedly, he testified that the hackers got the SMS verification via voicemail. It is quite easy to get access to voicemail because many people do not remember to set up 4-digit codes. Whereas, people setting 4-digit codes can feel disappointed because of miscreants along with their tools at the disposal in case they want. Whilst voicemail has been designed to check whether the accessing call’s number belongs to their subscriber or not, it is easier for those numbers to be “spoofed” when the hacker gets the right one.
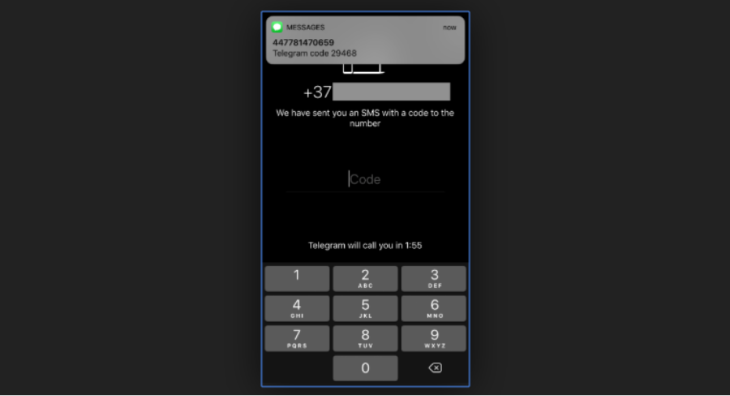
Therefore, the hackers, who can gain entry to voicemail, can also get access to Telegram’s SMS verification because those verification messages are sent to the victim’s voicemail when he or she cannot answer three times in a row or is having a call.
At DEFCON 2018, a presentation stated that Telegram isn’t the only security service that may be susceptible to this kind of risk. Any security service which allows verification messages to be sent through voicemail is endangered.
Ways to protect each user from these attacks
After Telegram has seen the vulnerability, the company has already updated to prevent these attacks. Now, users can request a code for login via a phone call only after 2-step verification which requires a code and password.
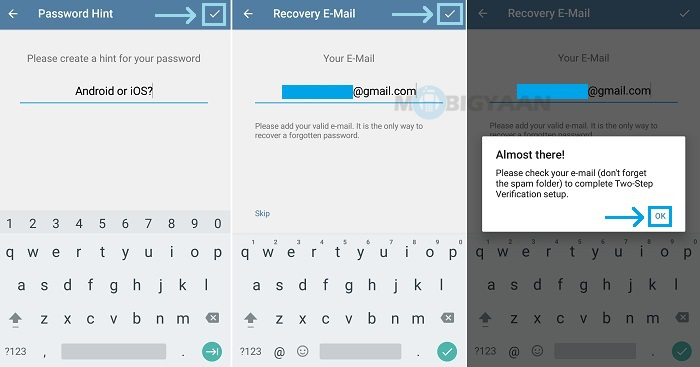
The report said it's advisable for users to turn on 2-factor or 2-step verification (if available) for any messaging service that they use. Moreover, in case the user is accidentally using voicemail, they should ensure that the voicemail is protected with a randomly generated PIN.
Featured Stories

How To - Mar 04, 2026
Getting Started with AI: A Newbie's Simple Guide

ICT News - Mar 03, 2026
Budget Entry-Level PCs Under $500 to Vanish by 2028 Due to Memory Price Surge

ICT News - Mar 02, 2026
IDC Report Predicts Surging Smartphone Prices Due to Global RAM Shortage

ICT News - Mar 01, 2026
Samsung Links Galaxy S26 Price Hikes to AI Memory Supply Issues

ICT News - Feb 28, 2026
Anthropic Blacklisted by US Department of War: Trump Orders Federal Ban Over AI...

ICT News - Feb 26, 2026
AI Models Frequently Resort to Nuclear Escalation in Simulated Crises, Study...

ICT News - Feb 23, 2026
It's Over for Xbox: Asha Sharma Takes Over to Ruin Microsoft Gaming with AI

ICT News - Feb 22, 2026
Which AI Model Excels at Which Task in 2026: A Comprehensive Guide

ICT News - Feb 21, 2026
AI Coding Agent Causes Major AWS Outage at Amazon

ICT News - Feb 20, 2026
Tech Leaders Question AI Agents' Value: Human Labor Remains More Affordable
Read more

ICT News- Mar 02, 2026
IDC Report Predicts Surging Smartphone Prices Due to Global RAM Shortage
This development underscores the broader ripple effects of the AI boom on everyday technology, highlighting the interconnected nature of global semiconductor supply chains.

ICT News- Mar 03, 2026
Budget Entry-Level PCs Under $500 to Vanish by 2028 Due to Memory Price Surge
The era of the sub-$500 PC appears to be ending.

How To- Mar 04, 2026
Getting Started with AI: A Newbie's Simple Guide
Are you curious about artificial intelligence but not sure where to begin? You are not alone.
Comments
Sort by Newest | Popular