Microsoft Partners with CBI to Bust Major Tech Support Scam Operation
Karamchand - Jun 08, 2025

CBI arrests six people and shuts down two illegal call centers running tech support scams against Japanese citizens with Microsoft's assistance.
- Exposed By UK Hacker, CEO Of Gurugram’s Scam Call Center Arrested
- 22-Year-Old Scammer Sending Fake Official Emails Arrested In Bengaluru
- Fake Dating Site Scams 65-Year-Old Man Rs 73 Lakh
India's Central Bureau of Investigation (CBI) has successfully dismantled a sophisticated international cybercrime network. The operation targeted Japanese citizens through fake technical support services. Moreover, the investigation revealed the complex structure of modern cybercrime operations.
Six individuals have been arrested in connection with the transnational scam. Additionally, authorities shut down two illegal call centers operating across multiple Indian states. The collaborative effort involved international partners and technology companies.

Operation Chakra V: Coordinated Law Enforcement Action
Multi-State Raids and Arrests
The CBI conducted coordinated searches across 19 locations on May 28, 2025. These operations spanned Delhi, Haryana, and Uttar Pradesh simultaneously. Furthermore, the raids formed part of Operation Chakra V, which specifically targets cyber-enabled financial crimes.
Law enforcement agencies seized valuable evidence during the operation. This included computers, storage devices, digital video recorders, and mobile phones. Consequently, investigators now possess substantial digital evidence to support their case.
International Collaboration
The investigation benefited from strong international partnerships throughout the process. The National Police Agency of Japan provided crucial assistance to Indian authorities. Similarly, Microsoft's cybersecurity team contributed technical expertise and intelligence.
This collaboration enabled authorities to track down perpetrators and understand their operational structure. Therefore, the success demonstrates the importance of cross-border cooperation in combating cybercrime.
Sophisticated Scam Targeting Japanese Citizens
Deceptive Call Center Operations
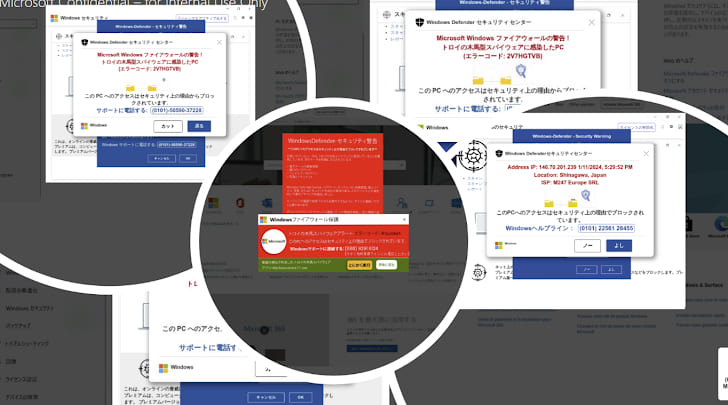
The criminal syndicate operated call centers designed to appear legitimate. Scammers impersonated technical support personnel from various multinational corporations, including Microsoft. These fraudsters specifically targeted Japanese citizens through carefully crafted social engineering tactics.
Victims were deceived into believing their electronic devices had been compromised. Subsequently, scammers coerced victims into transferring funds into mule accounts. The operation leveraged advanced social engineering techniques and technical subterfuge to extract money.
Advanced Criminal Techniques
The cybercrime network employed sophisticated methods to enhance their operations. Criminals used generative AI technology to scale their fraudulent activities effectively. Additionally, they utilized AI to identify potential victims and automate malicious pop-up creation.
Language translation capabilities allowed scammers to target Japanese victims specifically. These technological enhancements demonstrate the evolving nature of modern cybercrime operations. Consequently, law enforcement agencies must adapt their strategies accordingly.
Microsoft's Role in Investigation
Technical Support and Intelligence
Microsoft played a crucial role in identifying and tracking the criminal network. The company worked closely with the Japan Cybercrime Control Center (JC3) throughout the investigation. This partnership enabled authorities to uncover the fake technical support scam's full scope.
Steven Masada from Microsoft emphasized the global nature of modern cybercrime. He noted that cybercrime-as-a-service has increased connectivity among criminals worldwide. Therefore, addressing these threats requires coordinated international efforts.
Domain Takedown Operations
Microsoft's cybersecurity team has been actively combating similar scams globally. The company has taken down approximately 66,000 malicious domains and URLs since May 2024. These takedowns significantly disrupted criminal operations worldwide.
The cross-sector collaboration revealed the broader network behind these operations. This includes pop-up creators, search-engine optimizers, lead generators, and payment processors. Additionally, logistics providers and talent recruiters formed part of the criminal ecosystem.
Broader Criminal Network Structure
Cybercrime-as-a-Service Model
The investigation revealed how modern cybercrime operates as a service-based business model. Different specialists contribute specific skills to the overall criminal enterprise. These include technical expertise, marketing, logistics, and financial services.
This distributed approach makes cybercrime operations more resilient and harder to detect. However, it also creates more potential points of failure for law enforcement. Consequently, investigators can target multiple aspects of the criminal ecosystem simultaneously.
Evolving Threat Landscape
The use of generative AI represents a significant evolution in cybercrime tactics. Criminals can now automate many aspects of their operations more effectively. This includes victim identification, content creation, and language translation services.
These developments highlight the increasingly sophisticated nature of modern cyber threats. Furthermore, they underscore the importance of proactive global collaboration in protecting potential victims.
Recent Cybercrime Developments
Coinbase Data Breach Connection
The CBI operation comes shortly after revelations about a major cryptocurrency exchange breach. Reuters reported that Coinbase's recent data breach involved India-based customer support representatives. TaskUs employees were allegedly bribed to steal customer data from the exchange.
The breach was first identified in January 2025, leading to immediate action. TaskUs fired two employees for illegally accessing Coinbase customer information. Subsequently, Coinbase terminated its contract with the company entirely.
International CSAM Operation
Recent months have seen increased international cooperation against various cybercrimes. Between March and May 2025, authorities arrested 20 suspects across 12 countries. These arrests targeted individuals involved in creating and distributing child sexual abuse material.
Spanish authorities arrested seven suspects, including healthcare workers and teachers. Additionally, 10 suspects were arrested across various Latin American countries. INTERPOL identified 68 additional suspects for further investigation.
Implications for Cybersecurity
Importance of International Cooperation
The successful CBI operation demonstrates the critical importance of international collaboration. Modern cybercrime transcends national boundaries and requires coordinated responses. Furthermore, technology companies must actively participate in these efforts.
The partnership between Indian authorities, Japanese police, and Microsoft proved highly effective. This model should be replicated for other cybercrime investigations worldwide. Additionally, information sharing between agencies enhances overall security.
Evolution of Criminal Tactics
Cybercriminals continue to adopt new technologies to enhance their operations. The use of AI for victim targeting and content creation represents a significant escalation. Therefore, law enforcement agencies must develop corresponding technological capabilities.
The sophisticated nature of these operations requires specialized expertise and resources. Consequently, international cooperation becomes even more crucial for effective law enforcement. Organizations must invest in cybersecurity training and technology.
Future Outlook
Continued Vigilance Required
The dismantling of this criminal network represents a significant victory for international law enforcement. However, other similar operations likely continue operating worldwide. Therefore, continued vigilance and proactive measures remain essential.
Technology companies must maintain their collaboration with law enforcement agencies. Additionally, international partnerships should be strengthened to address emerging threats. The success of Operation Chakra V provides a valuable template for future operations.
Protecting Potential Victims
Public awareness campaigns should educate citizens about these sophisticated scam tactics. Potential victims need to understand how criminals exploit technology and social engineering. Furthermore, reporting mechanisms should be easily accessible and well-publicized.
The collaboration between public and private sectors proves essential for comprehensive cybersecurity. This partnership model should be expanded to address other types of cyber threats. Ultimately, protecting citizens requires coordinated efforts from all stakeholders involved.
Featured Stories

ICT News - Mar 03, 2026
Budget Entry-Level PCs Under $500 to Vanish by 2028 Due to Memory Price Surge

ICT News - Mar 02, 2026
IDC Report Predicts Surging Smartphone Prices Due to Global RAM Shortage

ICT News - Mar 01, 2026
Samsung Links Galaxy S26 Price Hikes to AI Memory Supply Issues

ICT News - Feb 28, 2026
Anthropic Blacklisted by US Department of War: Trump Orders Federal Ban Over AI...

ICT News - Feb 26, 2026
AI Models Frequently Resort to Nuclear Escalation in Simulated Crises, Study...

ICT News - Feb 23, 2026
It's Over for Xbox: Asha Sharma Takes Over to Ruin Microsoft Gaming with AI

ICT News - Feb 22, 2026
Which AI Model Excels at Which Task in 2026: A Comprehensive Guide

ICT News - Feb 21, 2026
AI Coding Agent Causes Major AWS Outage at Amazon

ICT News - Feb 20, 2026
Tech Leaders Question AI Agents' Value: Human Labor Remains More Affordable

ICT News - Feb 19, 2026
Escalating Costs for NVIDIA RTX 50 Series GPUs: RTX 5090 Tops $5,000, RTX 5060 Ti...
Read more

ICT News- Mar 03, 2026
Budget Entry-Level PCs Under $500 to Vanish by 2028 Due to Memory Price Surge
The era of the sub-$500 PC appears to be ending.

ICT News- Mar 02, 2026
IDC Report Predicts Surging Smartphone Prices Due to Global RAM Shortage
This development underscores the broader ripple effects of the AI boom on everyday technology, highlighting the interconnected nature of global semiconductor supply chains.

ICT News- Mar 01, 2026
Samsung Links Galaxy S26 Price Hikes to AI Memory Supply Issues
This development highlights the broader challenges faced by the tech industry as it integrates artificial intelligence into everyday consumer electronics.
Comments
Sort by Newest | Popular