Several Big Names In Tech Have Partnered Up To Improve Cloud Security
Chitanis - Aug 27, 2019

Some big names in tech have partnered to create the Confidential Computing Consortium, in order to promote security standards to protect data in use
- Google Has Resolved Cloud Outage But Its Impact On Cloud Computing Atmosphere Still Exists
- AI Gives A 'Magic Pill' For Indian, Solves Any Disease
- Oracle Fired 100 Indian Employees And Here Are The Reasons
Several big names in the technology industry have partnered to create the Confidential Computing Consortium (CCC), in a new effort to promote security standards to better protect data in use.
The CCC was announced at Open Source Summit on Wednesday. The founding members including Google Cloud, Microsoft, Intel, Alibaba Cloud, IBM, Arm, Baidu, Tencent, Swisscom, and Red Hat.

The Need For The Confidential Computing Consortium
Currently, the cloud is growing rapidly, leading to risks from data leakage and loss. In the 2019 Cloud Security Report, cybersecurity firm Check Point said that unauthorized access to the cloud and account hijacking are some of the major vulnerabilities of cloud. It also emphasized the need for stronger authentication mechanisms to protect users’ personal data against those attacks. That's the reason why the CCC was established.
What Is Confidential Computing?
According to Mark Russinovich, a CTO of Microsoft Azure, we need to protect data against three types of data exposure. They are data in use, data in transit, and data at rest. Confidential computing will target the first type.
By using this technology, organizations will be able to collaborate securely on multi-party datasets and get shared insights without access to those data.
The Key Part Of Confidential Computing
A crucial part of confidential computing is using a trusted execution environment (TEE), also known as secure enclaves, which ensure security and integrity of data and code in the processor.
The CCC will use solutions like Microsoft Open Enclave Software Development Kit (SDK), Red Hat Enarx and Intel Software Guard Extensions (SGX) for helping to protect sensitive data and software against modification by bad actors.
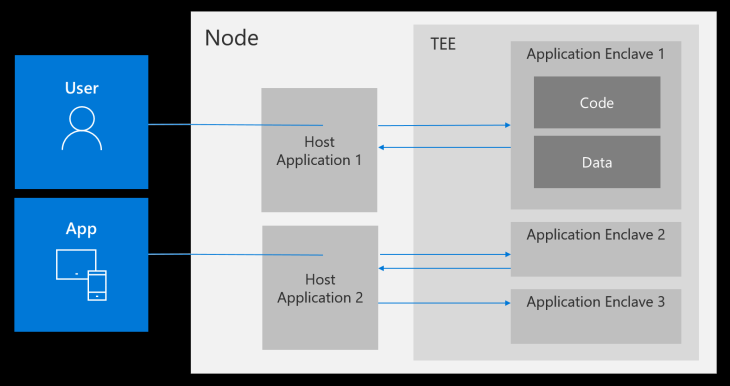
Signal, a messaging app that supports end-to-end encryption, uses SGX to keep its user’s address book safe by determining if contacts are also Signal users or not, without disclosing contact details to Signal service.
Google and Apple do the same, making use of TEE in phones for storing confidential data on the device like payment information or passwords.
Where Is Google’s Asylo?
A lot of people may wonder why Asylo framework didn’t join the CCC. Last year, Google announced this cloud platform to develop apps using TEEs. However, with the current version 0.4, the solution seems to be a work in progress. Other efforts that focused on privacy like Private Join and Compute and Federated Learning were also absent.
What Is Next?
There is no doubt about the confidential computing’s potential. Organizations increasingly move to the cloud, so we need a platform-agnostic solution to keep data private in it. The CCC wants to promote developers to build software which can be deployed on different TEEs.
Featured Stories

How To - Mar 04, 2026
Getting Started with AI: A Newbie's Simple Guide

ICT News - Mar 03, 2026
Budget Entry-Level PCs Under $500 to Vanish by 2028 Due to Memory Price Surge

ICT News - Mar 02, 2026
IDC Report Predicts Surging Smartphone Prices Due to Global RAM Shortage

ICT News - Mar 01, 2026
Samsung Links Galaxy S26 Price Hikes to AI Memory Supply Issues

ICT News - Feb 28, 2026
Anthropic Blacklisted by US Department of War: Trump Orders Federal Ban Over AI...

ICT News - Feb 26, 2026
AI Models Frequently Resort to Nuclear Escalation in Simulated Crises, Study...

ICT News - Feb 23, 2026
It's Over for Xbox: Asha Sharma Takes Over to Ruin Microsoft Gaming with AI

ICT News - Feb 22, 2026
Which AI Model Excels at Which Task in 2026: A Comprehensive Guide

ICT News - Feb 21, 2026
AI Coding Agent Causes Major AWS Outage at Amazon

ICT News - Feb 20, 2026
Tech Leaders Question AI Agents' Value: Human Labor Remains More Affordable
Read more

How To- Mar 04, 2026
Getting Started with AI: A Newbie's Simple Guide
Are you curious about artificial intelligence but not sure where to begin? You are not alone.

ICT News- Mar 03, 2026
Budget Entry-Level PCs Under $500 to Vanish by 2028 Due to Memory Price Surge
The era of the sub-$500 PC appears to be ending.


Comments
Sort by Newest | Popular