Biggest Shame Of The Year: Iranian Hackers Accidentally Leaked Videos Showing Them Hacking
Aadhya Khatri - Jul 20, 2020

According to researchers of IBM’s X-Force, they recently got their hands on 5-hour long footage recording the screen of some hackers working for ITG18
- Hackers Purposely Upload Their Fingerprints To Crime Scene - One Of The Dumbest Hacks Ever
- A Japanese Sex Hotel App Was Hacked, A Real Disaster For Its Customers
- Even Two-Factor Authentication Couldn't Stop Chinese Hackers
Security researchers usually have only thin trails of evidence to follow to trace a state-sponsored hacking operation.
However, their job just got a lot easier with a group of Iranian hackers who recorded everything they do and posted the video to an unprotected server.
According to researchers of IBM’s X-Force, they recently got their hands on 5-hour long footage recording the screen of some hackers working for ITG18. This group is also known as Charming Kitten or APT35.
It is one of the most active espionage teams with sponsors from the Iranian government. The video and other clues prove that the hackers attacked an Iranian-American philanthropist and some US State Department staff.
As stated by the IBM experts, the footage was exposed because of a security setting misconfiguration of a virtual private cloud server they kept track of in some previous hacking attempts of APT35.
Just when IBM researchers were keeping an eye on the server, the files, including the video, were uploaded. The footage is apparently training material for junior hackers, showing them how to deal with the hacked accounts.
While the work shown in the video is far from being anything sophisticated, rather a labor-intensive task important for any operation, it shows a first-hand view of how a state-sponsored hacking attempt was executed.
The two videos IBM got demonstrated the process of siphoning data from a hacked account. One of them shows hackers logging into a dummy Gmail account with credentials from a text document. Next, they linked it to Zimbra, an email software to manage several accounts from one interface.
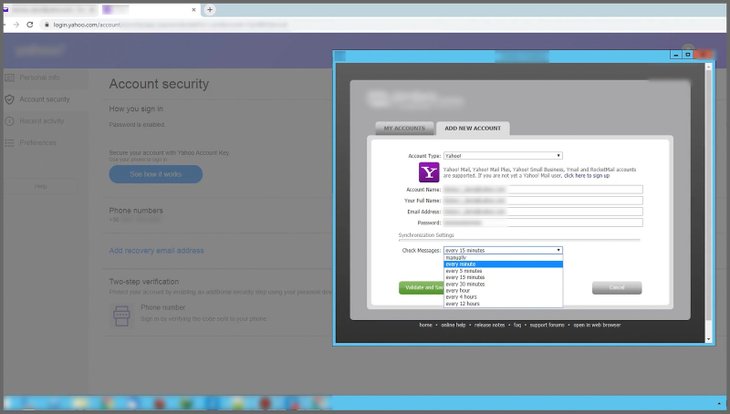
With Zimbra, the hackers were able to save all inbox’s information to their computers. The next step was to delete the notification saying Gmail permission has been changed. What comes next was saving victims’ contacts and photos. The other video demonstrates the same process for a Yahoo account.
Data stored in a Google account was stolen in less than four minutes while it takes only three minutes to do the same for a Yahoo account. However, in real life with tens of hundreds of gigabytes of data, hackers may have to spend more time than that.
This isn’t the first time hackers left behind evidence of their work but according to former NSA staffer Emily Crose, this is a rare win for the defenders as it wasn’t until now that we had actual video of state-sponsored hacking attempts, which could force the espionage team to change their tactics.
According to IBM, this discovery won’t slow down the pace of hacking. Last year, Microsoft seized close to a hundred domains and that did little to prevent the hackers from doing their job.
So if that kind of infrastructure purge couldn’t do anything, a few leaked videos won’t either.
>>> Hackers Reportedly Earn 120,000$ From Hacking Major Twitter Accounts
Featured Stories

Features - Jan 29, 2026
Permanently Deleting Your Instagram Account: A Complete Step-by-Step Tutorial

Features - Jul 01, 2025
What Are The Fastest Passenger Vehicles Ever Created?

Features - Jun 25, 2025
Japan Hydrogen Breakthrough: Scientists Crack the Clean Energy Code with...

ICT News - Jun 25, 2025
AI Intimidation Tactics: CEOs Turn Flawed Technology Into Employee Fear Machine

Review - Jun 25, 2025
Windows 11 Problems: Is Microsoft's "Best" OS Actually Getting Worse?

Features - Jun 22, 2025
Telegram Founder Pavel Durov Plans to Split $14 Billion Fortune Among 106 Children

ICT News - Jun 22, 2025
Neuralink Telepathy Chip Enables Quadriplegic Rob Greiner to Control Games with...

Features - Jun 21, 2025
This Over $100 Bottle Has Nothing But Fresh Air Inside

Features - Jun 18, 2025
Best Mobile VPN Apps for Gaming 2025: Complete Guide

Features - Jun 18, 2025
A Math Formula Tells Us How Long Everything Will Live
Read more

Mobile- Feb 16, 2026
Xiaomi Launches Affordable Tracker to Compete with Apple's AirTag
For users tired of ecosystem lock-in or high prices, the Xiaomi Tag represents a compelling, no-frills option that delivers core functionality at a fraction of the cost.

ICT News- Feb 18, 2026
Google's Project Toscana: Elevating Pixel Face Unlock to Rival Apple's Face ID
As the smartphone landscape evolves, Google's push toward superior face unlock technology underscores its ambition to close the gap with Apple in user security and convenience.

Mobile- Feb 17, 2026
Anticipating the Samsung Galaxy S26 and S26+: Key Rumors and Specs
The Samsung Galaxy S26 series is on the horizon, sparking excitement among tech enthusiasts.
Comments
Sort by Newest | Popular