Hackers Can Still Hack Your Accounts Even When You Use Two-Factor Authentication
Dhir Acharya - Mar 12, 2020
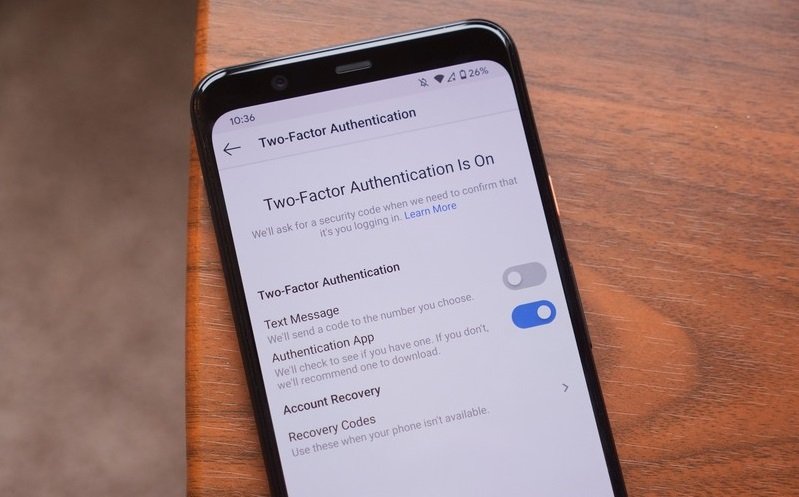
Two-factor authentication is believed to be a good way to prevent hackers from attacking our phones and accounts. But there are ways to overcome 2FA.
- Google to Phase Out SMS-Based Authentication Codes
- Apple Engineers Come Up With Easier Two-Factor Authentication
- 5 Best Authenticator Apps To Protect Your Accounts
You’re always advised to use two-factor authentication to cause more difficulties to hackers and protect your accounts better. Once you use two-factor authentication, you will get a code pair with your password through SMS or generated by an app.
The problem is that this doesn’t always work. Hackers once hacked Twitter account of Jack Dorsey, Twitter Chief Executive, with an IM swap attack. The attack tricked the phone's carrier to switch the mobile service to another device.
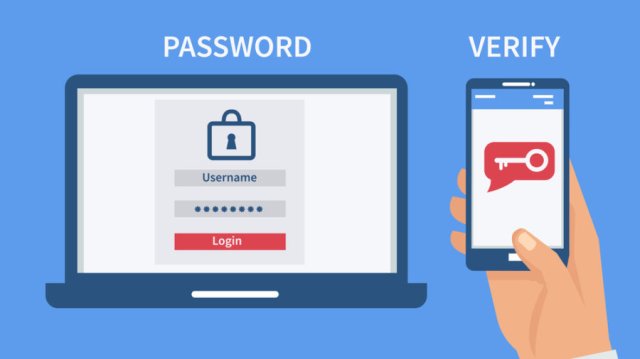
There are more and more online services like e-banking or social networks advising their users to use two-factor authentication to avoid hacking and data stealing. Millions of passwords have been leaked. A lot of us often reuse old passwords and that makes our account easier to be hacked.
It doesn’t mean you have to stop two-factor authentication. It is still very important and helpful to protect your accounts although it may be a little annoying and take more time to log in. Combining many factors with different qualities always makes it harder for hackers to steal your data.
Authentication code interception
Two-factor authentication is helpful but it is not as strong as you expect. Even when your password is used in a short time, hackers can still steal them. If hackers can hit your password lock, they can beat your security as well.
A lot of fake websites are created to collect your information. Modlishka is a new testing tool written by a security researcher. It indicates the phishing attack and shows how vulnerable websites are.
The hacker will send you an email with a link to a fake website that was created cleverly to look convincing. When you enter login details and the code you get by SMS or an authenticator app. The hackers will use that information to hack your account on the real website.
SIM swapping attacks

Another way to beat two-factor authentication is the SIM swap attack. The hacker will call to your carrier and pretend to be you and convince an employee of the carrier to switch services of your phone to another phone (obviously hacker’s phone). After your phone service is done moved, the hacker will be able to read your messages and get your authentication code as well.
Just because it is not perfect, doesn’t mean it is useless. Two-factor authentication is still better than just your passwords only, but you need to consider stronger ways to protect your accounts.
>>> 5 Best Authenticator Apps To Protect Your Accounts
Featured Stories

Features - Jan 29, 2026
Permanently Deleting Your Instagram Account: A Complete Step-by-Step Tutorial

Features - Jul 01, 2025
What Are The Fastest Passenger Vehicles Ever Created?

Features - Jun 25, 2025
Japan Hydrogen Breakthrough: Scientists Crack the Clean Energy Code with...

ICT News - Jun 25, 2025
AI Intimidation Tactics: CEOs Turn Flawed Technology Into Employee Fear Machine

Review - Jun 25, 2025
Windows 11 Problems: Is Microsoft's "Best" OS Actually Getting Worse?

Features - Jun 22, 2025
Telegram Founder Pavel Durov Plans to Split $14 Billion Fortune Among 106 Children

ICT News - Jun 22, 2025
Neuralink Telepathy Chip Enables Quadriplegic Rob Greiner to Control Games with...

Features - Jun 21, 2025
This Over $100 Bottle Has Nothing But Fresh Air Inside

Features - Jun 18, 2025
Best Mobile VPN Apps for Gaming 2025: Complete Guide

Features - Jun 18, 2025
A Math Formula Tells Us How Long Everything Will Live
Read more

Gadgets- Mar 08, 2026
Best Budget Keyboards of 2026
These budget keyboards prove that you don't need to spend hundreds for a quality typing experience in 2026.

Mobile- Mar 08, 2026
Transforming Android: New Desktop Mode Makes Phones PC-Capable
This update marks an exciting era for Android, empowering users to do more with their everyday devices.
Comments
Sort by Newest | Popular