Unintentionally, This Fitness Tracking App Revealed Secret Bases Of U.S Army
Anil - Apr 17, 2020

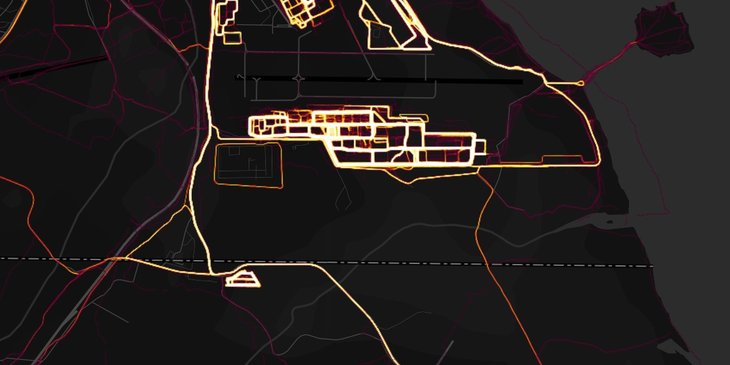
Strava’s heat map had provided adequate data to clearly specify and locate a number of secret locations belonging to the U.S army.
- Facebook Expect To Help Veterans Become Engineers Working On AR And VR Tech
- U.S. Military Is Secretly Funding Researches On Fringe Technologies
The popular fitness tracking app Strava recently was supposed to give away data about secret bases of the U.S army, patrols and forward operating bases (FOBs) as well.

The information originated from Twitter posts of Nathan Ruser, a founding member of the Institute for United Conflict Analysts. He emphasized that Strava’s heat map had provided adequate data to clearly specify and locate a number of secret locations belonging to the U.S army. In addition, he gave proof of his statement in his later tweets by identifying a Russian operating area in Khmeimim as well as their patrol, a Turkish patrol, Afghanistan FOBs, and soldier running routes.
As a result, the disclosure indicates that several dangers have a close connection with the development of the Internet of Things and unrestrained shadow IT. Added by the Twitter account Jake Williams, Strava users are made to autonomously allow their data to be shared on the heatmap; meanwhile, those who do not want to do so have to refuse the access rights manually.
In the enterprise, lax privacy policies can cause data revelation, which puts IP at high risk in some cases. According to Williams, the situation can have worse results than estimated. On his Twitter, he warned app developers that their defaults could bring deaths to their users.
In particular, the version of Strava’s heat map that appeared in Ruster’s analysis was launched in November 2017. As written in Strava blog post, it collects the data from 1 billion activities and 3 trillion latitude or longitude points (10TB of data totally). Although it is guaranteed that the data is kept anonymous, it does not ensure that hackers and cybercrimes can’t gain access to the data.
This data leakage should be considered as a dire warning to security and IT experts that even an app appearing to be harmless, a fitness tracker, for instance, can pose a threat to many organizations. From now on, enterprises will surely need to gain an IoT policy that is responsible for all devices used in the company’s network, not just includes the ones containing vulnerable data.
>>> Man Uses 99 Phones To Fake Traffic Jam On Google Maps
Featured Stories

Features - Jan 29, 2026
Permanently Deleting Your Instagram Account: A Complete Step-by-Step Tutorial

Features - Jul 01, 2025
What Are The Fastest Passenger Vehicles Ever Created?

Features - Jun 25, 2025
Japan Hydrogen Breakthrough: Scientists Crack the Clean Energy Code with...

ICT News - Jun 25, 2025
AI Intimidation Tactics: CEOs Turn Flawed Technology Into Employee Fear Machine

Review - Jun 25, 2025
Windows 11 Problems: Is Microsoft's "Best" OS Actually Getting Worse?

Features - Jun 22, 2025
Telegram Founder Pavel Durov Plans to Split $14 Billion Fortune Among 106 Children

ICT News - Jun 22, 2025
Neuralink Telepathy Chip Enables Quadriplegic Rob Greiner to Control Games with...

Features - Jun 21, 2025
This Over $100 Bottle Has Nothing But Fresh Air Inside

Features - Jun 18, 2025
Best Mobile VPN Apps for Gaming 2025: Complete Guide

Features - Jun 18, 2025
A Math Formula Tells Us How Long Everything Will Live
Read more

ICT News- Feb 18, 2026
Google's Project Toscana: Elevating Pixel Face Unlock to Rival Apple's Face ID
As the smartphone landscape evolves, Google's push toward superior face unlock technology underscores its ambition to close the gap with Apple in user security and convenience.

ICT News- Feb 20, 2026
Tech Leaders Question AI Agents' Value: Human Labor Remains More Affordable
In a recent episode of the All-In podcast, prominent tech investors and entrepreneurs expressed skepticism about the immediate practicality of deploying AI agents in business operations.

ICT News- Feb 19, 2026
Escalating Costs for NVIDIA RTX 50 Series GPUs: RTX 5090 Tops $5,000, RTX 5060 Ti Closes in on RTX 5070 Pricing
As the RTX 50 series continues to push boundaries in gaming and AI, these price trends raise questions about accessibility for average gamers.
Comments
Sort by Newest | Popular